Hello Friends,
Today i am discussing about Websploit Framework
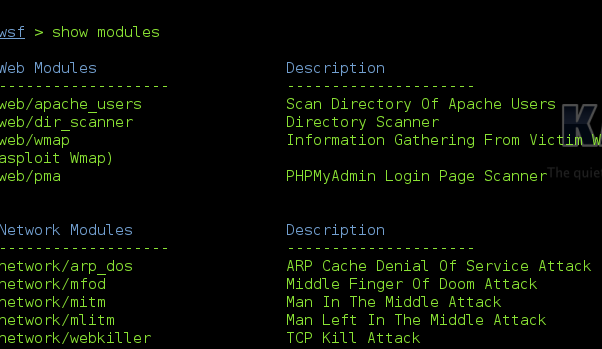
Websploit is an automatic vulnerability assessment, web crawler and exploiter tool. It is an open source command line utility that composed on modular structure. At the time of writing, there are 16 modules are available on Websploit, it can be downloaded from sourceforge project website but it is available on Kali Linux by default.
Websploit can be synchronize with Metasploit WMAP project for web vulnerability scanning, there are four categories of modular are available and they are:
Web Modules
Network Modules
Exploit Modules
Wireless Modules
In Wireless module we can run some interesting WiFi attacking vector including the WiFi jammer and WiFi DDOS attack. For exploitation, websploit is working on the basis of Metasploit Autopwn service and metasploit browser autopwn service. A large number of interesting attacking vectors are available on the network modules,
If you are on Kali Linux, then click on Applications ? Kali Linux ? Web Applications ? Web Vulnerability Scanners ? Websploit
The list of commands that can applicable on websploit are:
Today i am discussing about Websploit Framework
Websploit is an automatic vulnerability assessment, web crawler and exploiter tool. It is an open source command line utility that composed on modular structure. At the time of writing, there are 16 modules are available on Websploit, it can be downloaded from sourceforge project website but it is available on Kali Linux by default.
Websploit can be synchronize with Metasploit WMAP project for web vulnerability scanning, there are four categories of modular are available and they are:
Web Modules
Network Modules
Exploit Modules
Wireless Modules
If you are on Kali Linux, then click on Applications ? Kali Linux ? Web Applications ? Web Vulnerability Scanners ? Websploit
The list of commands that can applicable on websploit are: